Tability is a cheatcode for goal-driven teams. Set perfect OKRs with AI, stay focused on the work that matters.
What are Security Training OKRs?
The Objective and Key Results (OKR) framework is a simple goal-setting methodology that was introduced at Intel by Andy Grove in the 70s. It became popular after John Doerr introduced it to Google in the 90s, and it's now used by teams of all sizes to set and track ambitious goals at scale.
Writing good OKRs can be hard, especially if it's your first time doing it. You'll need to center the focus of your plans around outcomes instead of projects.
We understand that setting OKRs can be challenging, so we have prepared a set of examples tailored for Security Training. Take a peek at the templates below to find inspiration and kickstart your goal-setting process.
If you want to learn more about the framework, you can read our OKR guide online.
The best tools for writing perfect Security Training OKRs
Here are 2 tools that can help you draft your OKRs in no time.
Tability AI: to generate OKRs based on a prompt
Tability AI allows you to describe your goals in a prompt, and generate a fully editable OKR template in seconds.
- 1. Create a Tability account
- 2. Click on the Generate goals using AI
- 3. Describe your goals in a prompt
- 4. Get your fully editable OKR template
- 5. Publish to start tracking progress and get automated OKR dashboards
Watch the video below to see it in action 👇
Tability Feedback: to improve existing OKRs
You can use Tability's AI feedback to improve your OKRs if you already have existing goals.
- 1. Create your Tability account
- 2. Add your existing OKRs (you can import them from a spreadsheet)
- 3. Click on Generate analysis
- 4. Review the suggestions and decide to accept or dismiss them
- 5. Publish to start tracking progress and get automated OKR dashboards
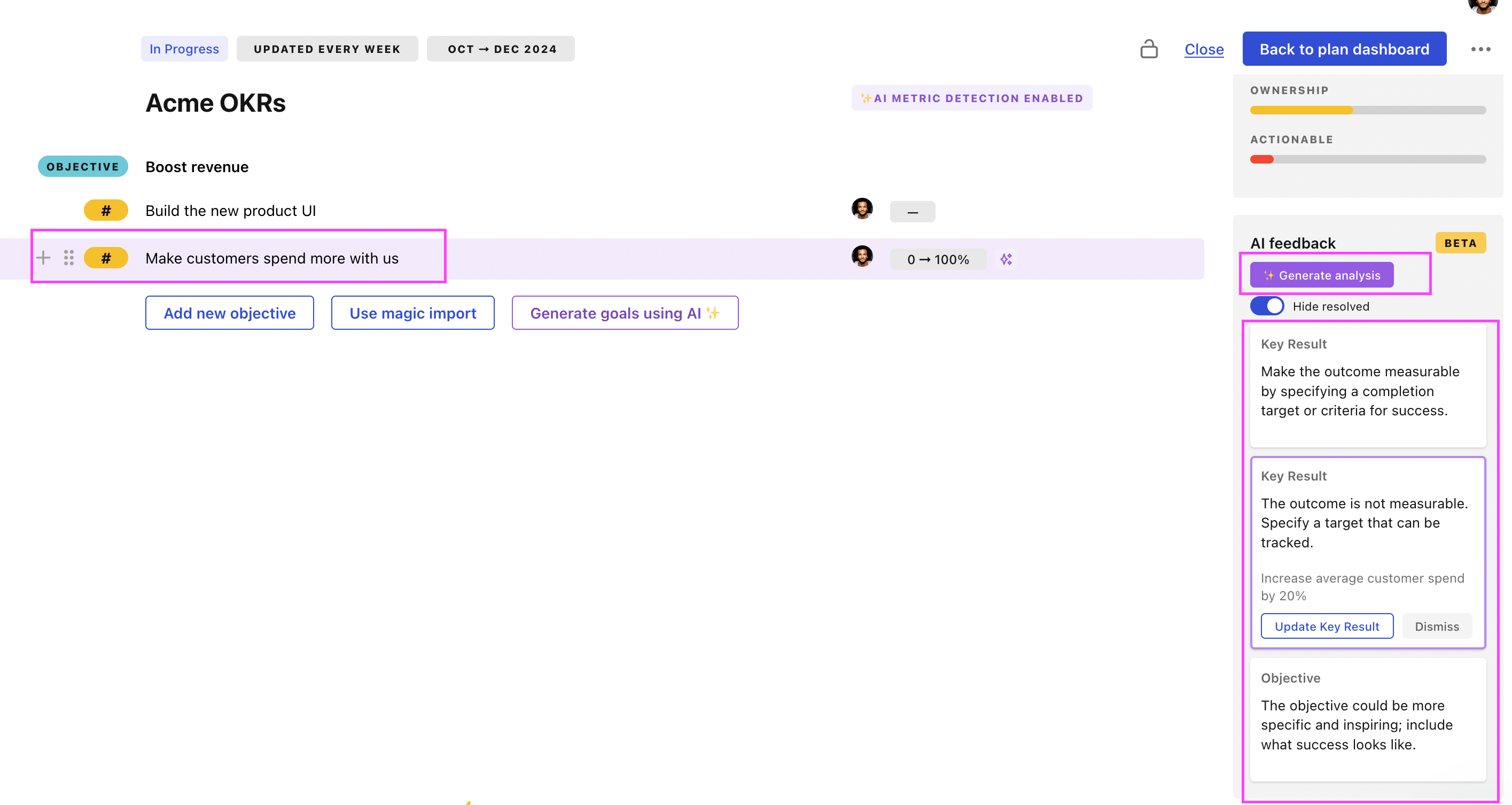
Tability will scan your OKRs and offer different suggestions to improve them. This can range from a small rewrite of a statement to make it clearer to a complete rewrite of the entire OKR.
Security Training OKRs examples
We've added many examples of Security Training Objectives and Key Results, but we did not stop there. Understanding the difference between OKRs and projects is important, so we also added examples of strategic initiatives that relate to the OKRs.
Hope you'll find this helpful!
OKRs to successfully complete annual security training
ObjectiveSuccessfully complete annual security training
KRApply learned procedures in simulated security scenarios with zero errors
Practice procedures until executed flawlessly
Review and memorize security procedures thoroughly
Engage in regular simulated security situations
KRAchieve a minimum of 85% score in end-of-training examination
Seek instructor feedback and clarification when needed
Review all training materials and take detailed notes
Complete daily self-assessments to track progress
KRComplete 100% of allocated course modules by end of quarter
Reserve dedicated study hours every day
Monitor progress regularly against targets
Set a weekly target for completing course modules
OKRs to implement comprehensive security training for all staff
ObjectiveImplement comprehensive security training for all staff
KRSuccessfully train 90% of staff through the newly launched security program
Schedule and implement regular training sessions
Develop concise, engaging materials for staff training
Identify key individuals for initial pilot of security program training
KRDevelop a detailed security training curriculum by engaging external consultants
Collaborate on curriculum details and learning objectives
Initiate a contract with chosen security consultant team
Identify reputable external consultants in security training development
KRAssess training effectiveness by improving security incident response time by 25%
Develop a benchmark for current security incident response times
Monitor and evaluate post-training response times
Implement advanced training techniques to improve reaction times
OKRs to enhance effectiveness of response processes for security incidents
ObjectiveEnhance effectiveness of response processes for security incidents
KRReduce average incident response time by 30%
Implement automated incident response software
Review and streamline incident report process
Enhance training of response team
KRConduct simulation exercises post-training to achieve at least 80% success rate
Monitor and measure success rates, aiming for 80% achievement
Implement simulation exercises regularly for all trained individuals
Develop a variety of simulation exercises relevant to the training content
KRImplement incident response training for 100% of the security team
Identify key incident response topics for comprehensive training
Develop interactive, practical training modules for the team
Schedule and conduct training sessions regularly
OKRs to implement Crowdstrike enterprise endpoint security with new features
ObjectiveImplement Crowdstrike enterprise endpoint security with new features
KRSuccessfully integrate Crowdstrike into 75% of enterprise endpoints by week 8
Install and configure Crowdstrike on identified endpoints
Identify and categorize 75% of enterprise endpoints for Crowdstrike integration
Conduct testing and troubleshooting post-integration
KRIdentify and document necessary Crowdstrike features for enterprise integration by week 4
Review Crowdstrike's offerings and identify essential features for enterprise integration
Establish a deadline for completing this task in week 4
Document the integration process with all essential features
KRConduct user training on Crowdstrike's new features for all key staff by week 12
Identify key staff for Crowdstrike's new features training
Develop comprehensive user training plan
Conduct training sessions by week 12
OKRs to embed security consciousness in business operations
ObjectiveEmbed security consciousness in business operations
KRReduce security breaches by 25% through rigorous employee training
Implement mandatory cybersecurity training for all employees
Schedule regular refresher courses on data protection
Update security policies and disseminate to staff
KREstablish a quarterly security audit to identify potential vulnerabilities
Schedule regular audits with a professional auditor
Define the scope of each quarterly security audit
Create a process to address identified vulnerabilities
KRAchieve 100% compliance on mandatory security awareness training by all employees
Organize regular training sessions for all personnel
Monitor and document each employee's training progress
Distribute security awareness training materials to all employees
OKRs to bolster Protection Against P1 Issues
ObjectiveBolster Protection Against P1 Issues
KRImprove first-time resolution rate for P1 issues to 70% across all teams
Train agents on P1 issue recognition and resolution
Implement P1 issue escalation protocol
Regularly review P1 resolution analytics
KRImplement a 25% reduction in P1 issues through improved security protocols
Train staff in improved security protocols
Identify vulnerabilities in current security protocols
Develop improved, stringent security measures
KRAchieve 90% staff training completion on new security measures by quarter end
Monitor and report staff training progress regularly
Schedule mandatory training sessions for all staff
Develop comprehensive security training program
OKRs to ensure full ISSO compliance through regular audits and security training
ObjectiveEnsure full ISSO compliance through regular audits and security training
KRTrain all new employees about ISSO compliance within their first week of employment
Schedule ISSO compliance training for new hires
Prepare relevant ISSO compliance materials
Conduct compliance training within their first week
KRIncrease the frequency of conducting audits to 100% every week from next quarter
Establish weekly audit schedule for consistent implementation
Monitor and track weekly audit outcomes constantly
Train audit team on the new weekly audit frequency
KRReduce security breaches by 90% through enhanced information security measures this quarter
Implement two-factor authentication for all system logins
Conduct regular cybersecurity training for staff
Update and strengthen all passwords regularly
OKRs to strengthen the company's network security defenses
ObjectiveStrengthen the company's network security defenses
KRTrain 90% of employees on new network security protocols within the next quarter
Assess current understanding of network security protocols among employees
Implement training, ensuring participation of at least 90% of employees
Develop comprehensive training program on new security protocols
KRImplement two-factor authentication for all user accounts by the end of next quarter
Purchase and set up chosen authentication system
Train users on new authentication system
Research best two-factor authentication systems for our needs
KRReduce the number of detected security breaches by 80% compared to last quarter
Implement an updated, top-quality cybersecurity system
Provide comprehensive cybersecurity training for all staff
Conduct regular, intensive IT security audits
OKRs to enhance the bank's IT security infrastructure
ObjectiveEnhance the bank's IT security infrastructure
KRImplement multi-factor authentication for 90% of bank's systems
Train IT staff on authentication tech installation and integration
Identify all systems currently lacking multi-factor authentication
Purchase needed hardware/software for multi-factor authentication implementation
KRConduct cybersecurity training for 100% of IT staff
Monitor and record staff training completion rates
Schedule training sessions for all IT staff
Identify and engage a reputable cybersecurity training provider
KRReduce system vulnerability by 30% with penetration testing and patching
Promptly patch identified system vulnerabilities
Analyze results to identify areas of weakness
Schedule regular penetration testing for system vulnerabilities
OKRs to upgrade and streamline physical security operations
ObjectiveUpgrade and streamline physical security operations
KRIncrease security coverage by 20% through additional surveillance systems
Investigate current surveillance system capabilities and limitations
Implement new surveillance systems accordingly
Research and identify potential additional surveillance technology
KRDecrease response times to security incidents by 25%
KRImplement a digital security management system with 100% staff training completion
Track and achieve 100% training completion
Choose a comprehensive digital security management system
Develop an all-staff training curriculum for the system
Security Training OKR best practices
Generally speaking, your objectives should be ambitious yet achievable, and your key results should be measurable and time-bound (using the SMART framework can be helpful). It is also recommended to list strategic initiatives under your key results, as it'll help you avoid the common mistake of listing projects in your KRs.
Here are a couple of best practices extracted from our OKR implementation guide 👇
Tip #1: Limit the number of key results
The #1 role of OKRs is to help you and your team focus on what really matters. Business-as-usual activities will still be happening, but you do not need to track your entire roadmap in the OKRs.
We recommend having 3-4 objectives, and 3-4 key results per objective. A platform like Tability can run audits on your data to help you identify the plans that have too many goals.
Tip #2: Commit to weekly OKR check-ins
Don't fall into the set-and-forget trap. It is important to adopt a weekly check-in process to get the full value of your OKRs and make your strategy agile – otherwise this is nothing more than a reporting exercise.
Being able to see trends for your key results will also keep yourself honest.
Tip #3: No more than 2 yellow statuses in a row
Yes, this is another tip for goal-tracking instead of goal-setting (but you'll get plenty of OKR examples above). But, once you have your goals defined, it will be your ability to keep the right sense of urgency that will make the difference.
As a rule of thumb, it's best to avoid having more than 2 yellow/at risk statuses in a row.
Make a call on the 3rd update. You should be either back on track, or off track. This sounds harsh but it's the best way to signal risks early enough to fix things.
Save hours with automated Security Training OKR dashboards
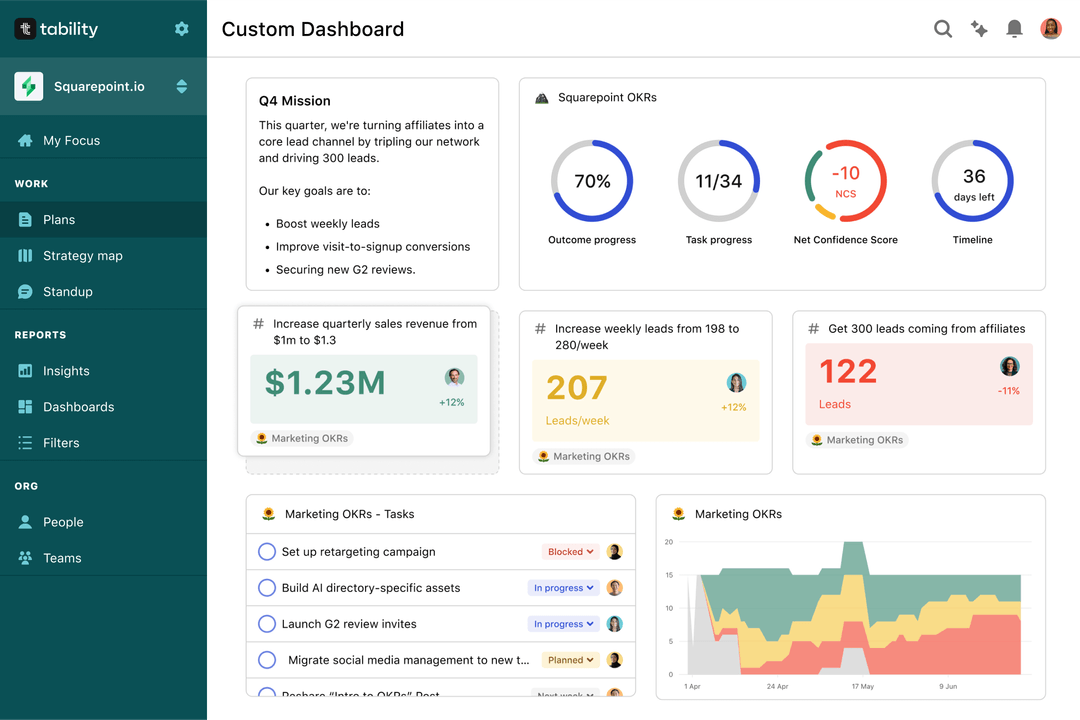
The rules of OKRs are simple. Quarterly OKRs should be tracked weekly, and yearly OKRs should be tracked monthly. Reviewing progress periodically has several advantages:
- It brings the goals back to the top of the mind
- It will highlight poorly set OKRs
- It will surface execution risks
- It improves transparency and accountability
Most teams should start with a spreadsheet if they're using OKRs for the first time. Then, you can move to Tability to save time with automated OKR dashboards, data connectors, and actionable insights.
How to get Tability dashboards:
- 1. Create a Tability account
- 2. Use the importers to add your OKRs (works with any spreadsheet or doc)
- 3. Publish your OKR plan
That's it! Tability will instantly get access to 10+ dashboards to monitor progress, visualise trends, and identify risks early.
More Security Training OKR templates
We have more templates to help you draft your team goals and OKRs.
OKRs to tackle technical debt
OKRs to boost global forecast accuracy
OKRs to establish comprehensive control mechanisms across all operations
OKRs to enhance my SCRUM proficiency
OKRs to enhance the efficiency of environmental risk management processes
OKRs to enhance knowledge and understanding through qualitative research