OKR template to achieve unbreachable security and absolute compliance in SOC operations
Your OKR template
The first component of this goal involves extensively training the entire IT staff on the most recent cybersecurity best practices. This involves identifying the best cybersecurity training programs for the staff, monitoring and recording their progress during the training, and enrolling all staff members in these selected training programs.
The next stage involves an audit, specifically a SOC2 Type 2 audit. The company aims to pass this audit without any exceptions. To reach this target, robust information security policies and controls will be implemented, pre-audit internal reviews will be carried out thoroughly, and a reputable third-party auditor specializing in SOC2 Type 2 will be hired.
The final part of the objective requires the implementation of a two-factor authentication across all system platforms. This will involve training employees on using the updated system, updating all system platforms to support the chosen two-factor authentication, and selecting an authentication provider suitable for the company's needs.
ObjectiveAchieve unbreachable security and absolute compliance in SOC operations
KRTrain 100% of IT staff on latest cybersecurity best practices
Identify top cybersecurity training programs for IT staff
Monitor and record training completion progress
Enroll all IT staff in selected training
KRSuccessfully complete a SOC2 Type 2 audit without any exceptions
Implement robust information security policies and controls
Conduct thorough pre-audit internal reviews
Hire a reputable third-party auditor specializing in SOC2 Type 2
KRImplement two-factor authentication across all system platforms
Train employees on how to use the updated two-factor authentication system
Update all system platforms to support chosen two-factor authentication
Select a two-factor authentication provider suitable for our needs
How to edit and track OKRs with Tability
You'll probably want to edit the examples in this post, and Tability is the perfect tool for it.
Tability is an AI-powered platform that helps teams set better goals, monitor execution, and get help to achieve their objectives faster.
With Tability you can:
- Use AI to draft a complete set of OKRs in seconds
- Connect your OKRs and team goals to your project
- Automate reporting with integrations and built-in dashboard
Instead of having to copy the content of the OKR examples in a doc or spreadsheet, you can use Tability’s magic importer to start using any of the examples in this page.
The import process can be done in seconds, allowing you to edit OKRs directly in a platform that knows how to manage and track goals.
Step 1. Sign up for a free Tability account
Go tohttps://tability.app/signup and create your account (it's free!)
Step 2. Create a plan
Follow the steps after your onboarding to create your first plan, you should get to a page that looks like the picture below.
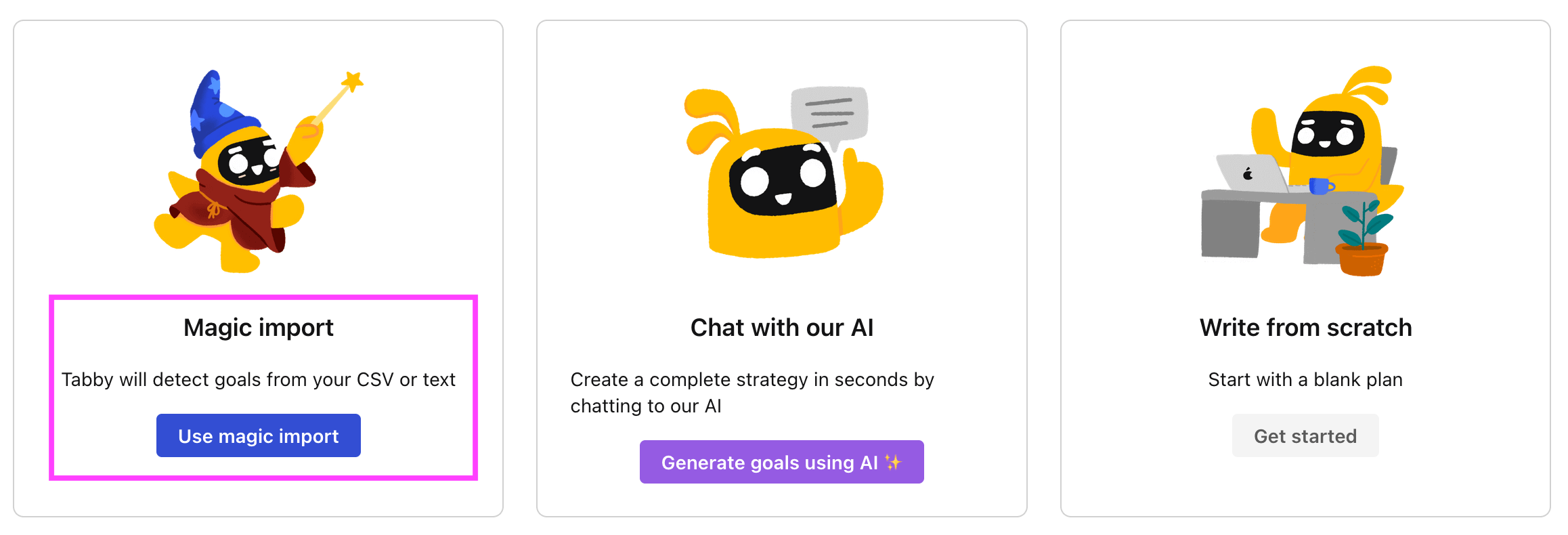
Step 3. Use the magic importer
Click on Use magic import to open up the Magic Import modal.
Now, go back to the OKR examples, and click on Copy on the example that you’d like to use.
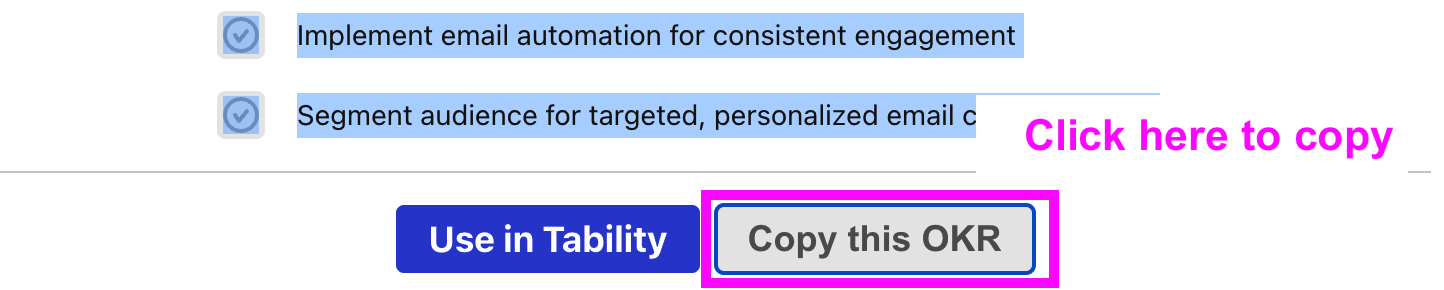
Paste the content in the text import section. Don’t worry about the formatting, Tability’s AI will be able to parse it!
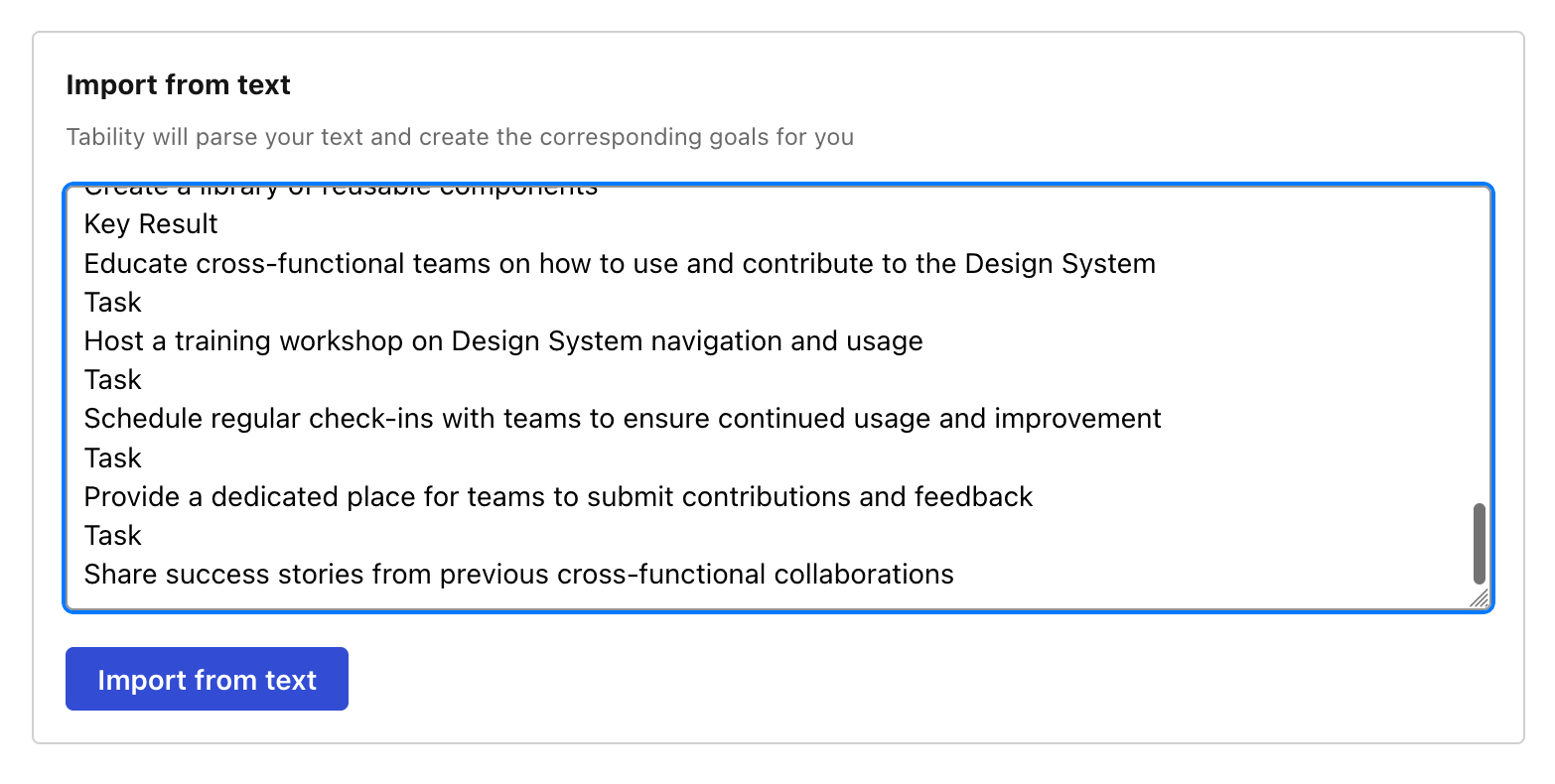
Now, just click on Import from text and let the magic happen.
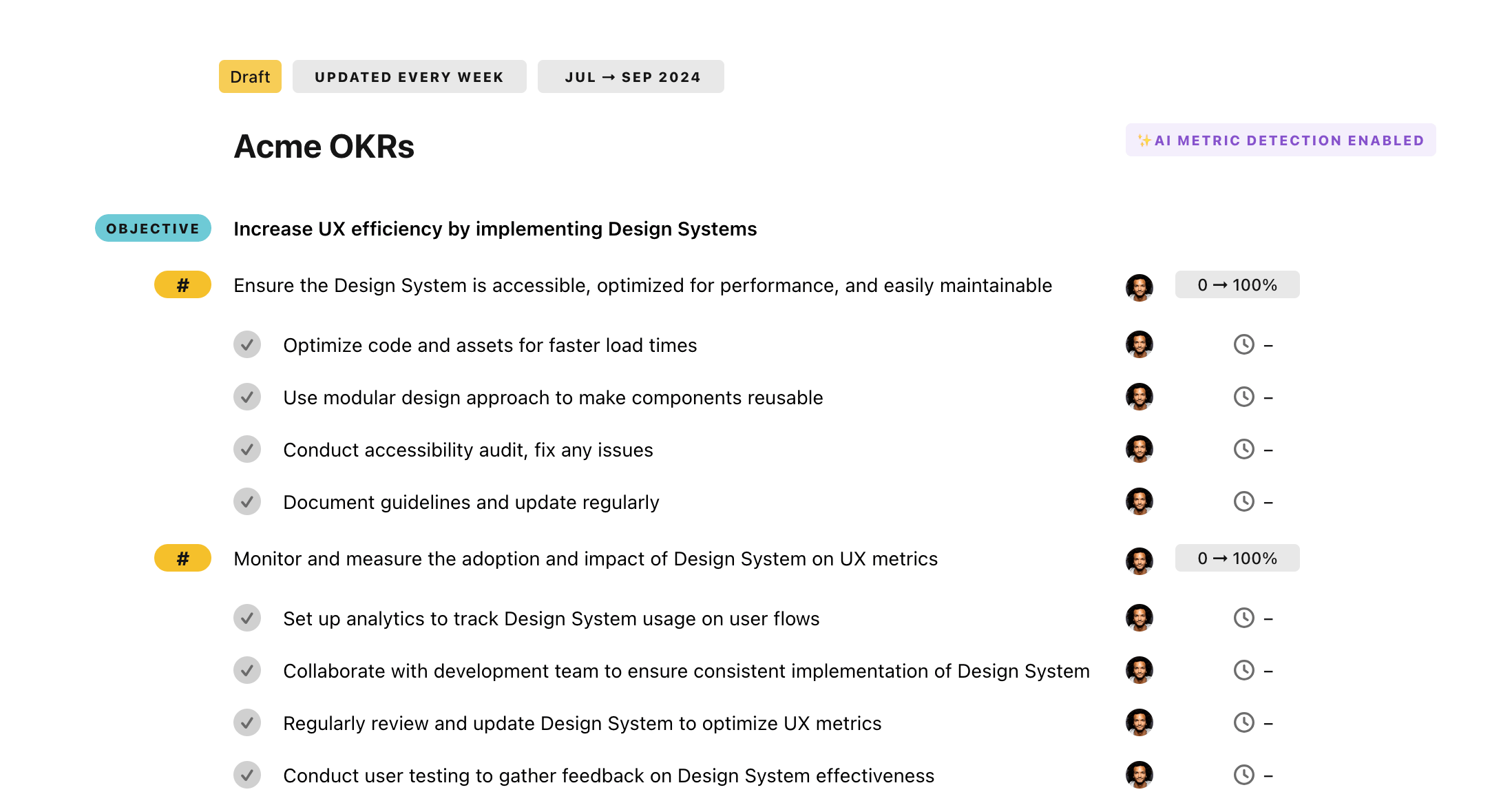
Once your example is in the plan editor, you will be able to:
- Edit the objectives, key results, and tasks
- Click on the target 0 → 100% to set better target
- Use the tips and the AI to refine your goals
Step 4. Publish your plan
Once you’re done editing, you can publish your plan to switch to the goal-tracking mode.
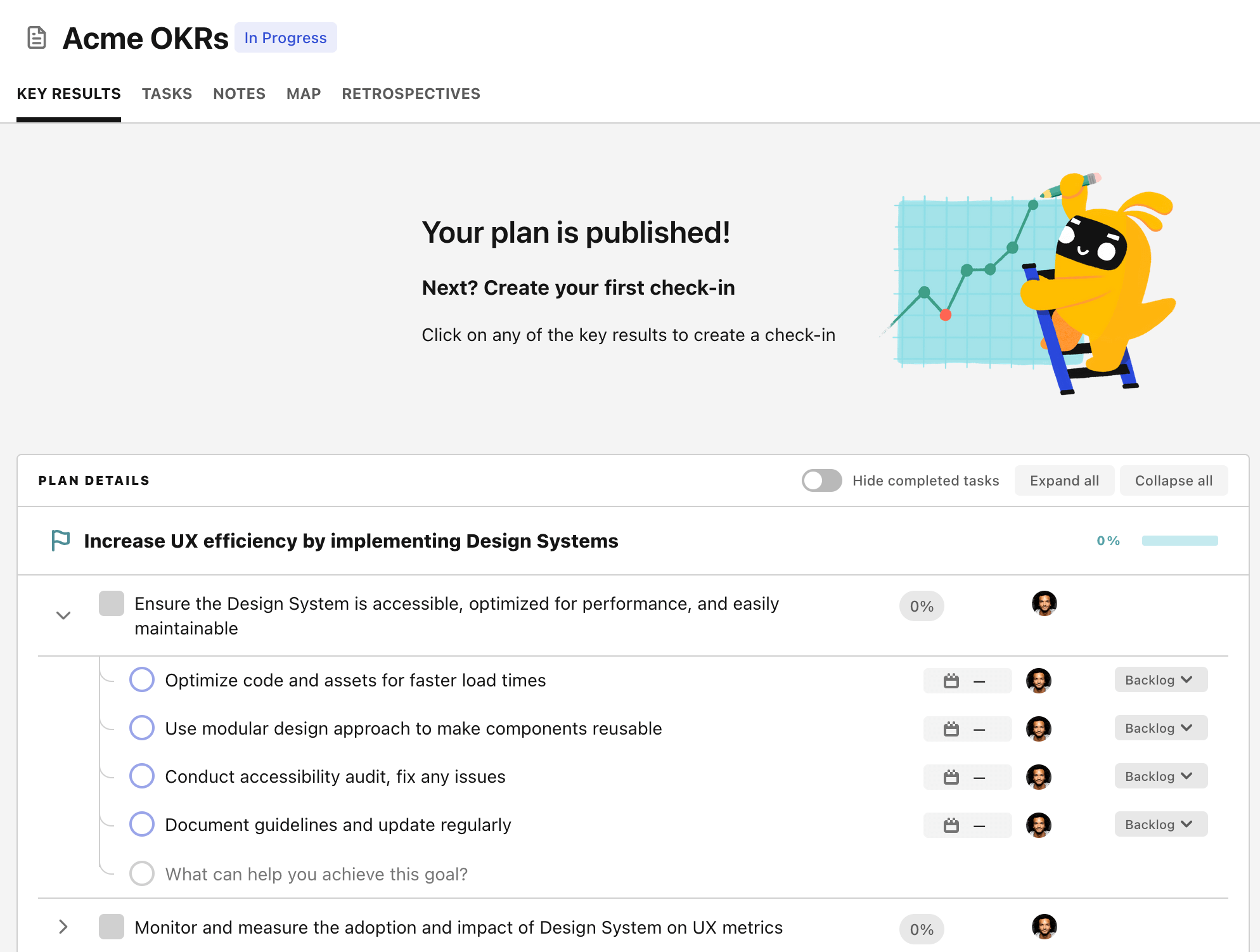
From there you will have access to all the features that will help you and your team save hours with OKR reporting.
- 10+ built-in dashboards to visualise progress on your goals
- Weekly reminders, data connectors, and smart notifications
- 9 views to map OKRs to strategic projects
- Strategy map to align teams at scale