Tability is a cheatcode for goal-driven teams. Set perfect OKRs with AI, stay focused on the work that matters.
What are Data Security OKRs?
The OKR acronym stands for Objectives and Key Results. It's a goal-setting framework that was introduced at Intel by Andy Grove in the 70s, and it became popular after John Doerr introduced it to Google in the 90s. OKRs helps teams has a shared language to set ambitious goals and track progress towards them.
Formulating strong OKRs can be a complex endeavor, particularly for first-timers. Prioritizing outcomes over projects is crucial when developing your plans.
To aid you in setting your goals, we have compiled a collection of OKR examples customized for Data Security. Take a look at the templates below for inspiration and guidance.
If you want to learn more about the framework, you can read our OKR guide online.
The best tools for writing perfect Data Security OKRs
Here are 2 tools that can help you draft your OKRs in no time.
Tability AI: to generate OKRs based on a prompt
Tability AI allows you to describe your goals in a prompt, and generate a fully editable OKR template in seconds.
- 1. Create a Tability account
- 2. Click on the Generate goals using AI
- 3. Describe your goals in a prompt
- 4. Get your fully editable OKR template
- 5. Publish to start tracking progress and get automated OKR dashboards
Watch the video below to see it in action 👇
Tability Feedback: to improve existing OKRs
You can use Tability's AI feedback to improve your OKRs if you already have existing goals.
- 1. Create your Tability account
- 2. Add your existing OKRs (you can import them from a spreadsheet)
- 3. Click on Generate analysis
- 4. Review the suggestions and decide to accept or dismiss them
- 5. Publish to start tracking progress and get automated OKR dashboards
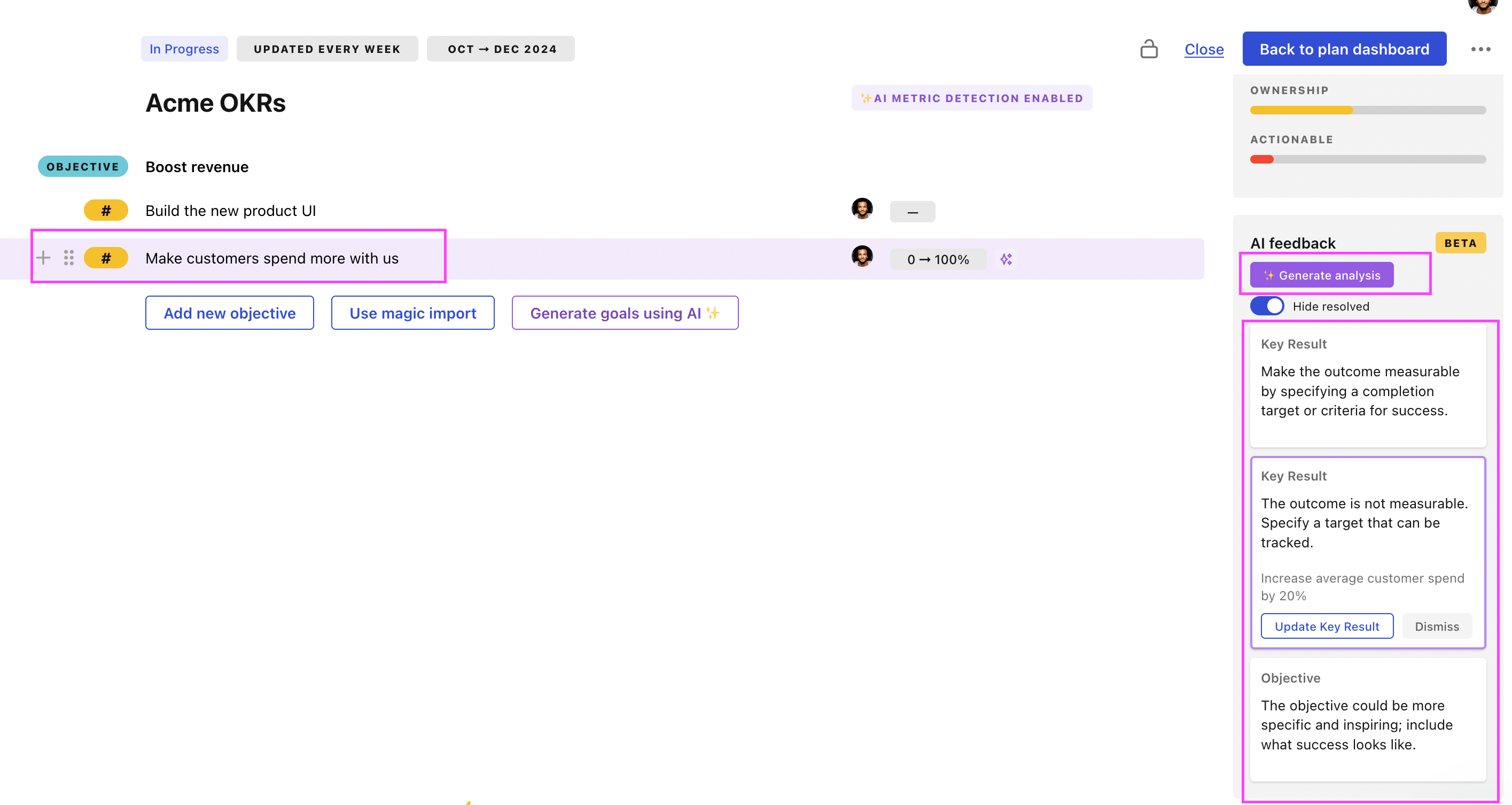
Tability will scan your OKRs and offer different suggestions to improve them. This can range from a small rewrite of a statement to make it clearer to a complete rewrite of the entire OKR.
Data Security OKRs examples
You'll find below a list of Objectives and Key Results templates for Data Security. We also included strategic projects for each template to make it easier to understand the difference between key results and projects.
Hope you'll find this helpful!
OKRs to implement SecOps playbooks for Abnormal security and Code42
ObjectiveImplement SecOps playbooks for Abnormal security and Code42
KRDesign, test, and implement the Abnormal Security playbook improving threat response time by 25%
Analyze current Abnormal Security playbook for improvements
Implement and monitor updated playbook in real-time
Design and test modifications for efficiency
KRIdentify and map 10 vital security processes for playbook integration by week 4
Map each process and its components
Identify 10 vital security processes for integration
Ensure integration within playbook by week 4
KRDevelop and enact the Code42 playbook, resulting in a 30% reduction in data loss incidents
Create and refine the comprehensive Code42 playbook
Implement and train staff on the Code42 playbook
Analyze existing data loss scenarios and identify potential vulnerabilities
OKRs to implement and maintain a comprehensive data protection program
ObjectiveStrengthen data protection program
KREnsure compliance with relevant data protection laws and regulations
Regularly review and update data protection practices
Develop and implement policies and procedures for compliance
Identify all applicable data protection regulations
Train employees on data protection laws and regulations
KRConduct a thorough risk assessment and mitigation plan
create contingency plan
develop mitigation strategies
assess likelihood and impact
identify potential risks
KRImplement regular employee training and awareness programs
Schedule regular training sessions
Identify training needs and design a program
Evaluate program effectiveness and make necessary improvements
Encourage employee participation and reward progress
KRRegularly review and update data protection policies and procedures
Train employees on updated policies and procedures
Document all data protection policies and procedures
Regularly audit adherence to policies and procedures
Assign responsibility for policy and procedure review and updates
OKRs to enhance security and compliance on kubernetes platform
ObjectiveEnhance security and compliance on kubernetes platform
KRIncrease traffic management efficiency by 40% to reduce potential risks
Implement advanced traffic control systems in high density areas
Develop efficient traffic scheduling and rerouting algorithms
Provide comprehensive training for traffic control staff
KRImplement 100% compliance with security regulations to ensure data protection
Train personnel on data security procedures
Develop a comprehensive data security protocol
Regularly audit for compliance adherence
KREnable automatic audit trails on 70% of the platform transactions for accountability
Configure settings to enable automatic audit trails
Identify 70% highest volume transactions on the platform
Test and implement the audit trail feature
OKRs to establish robust security controls for DHS/ATO and NATO contracts
ObjectiveEstablish robust security controls for DHS/ATO and NATO contracts
KRConduct quarterly maintenance on all the security controls and document findings
Document observations and any maintenance executed
Review all security control systems thoroughly
Perform necessary maintenance on security controls
KRImplement 5 new security measures aligned with DHS/ATO requirements by a 100%
Identify potential security measures that align with DHS/ATO requirements
Implement and test the newly identified security measures
Review existing security measures for any DHS/ATO non-compliance
KRAchieve zero security breaches related to the NATO contracts information
Implement strong encryption on all NATO-related digital communication
Train staff in counter-intelligence and data protection practices
Regularly perform rigorous security audits and fix vulnerabilities
OKRs to implement network DLP to limit disruption and data loss
ObjectiveImplement network DLP to limit disruption and data loss
KRIncrease DLP coverage across all critical systems by 60%
Regularly review and update DLP protection strategy
Implement DLP solutions on identified systems
Identify all critical systems lacking DLP protection
KREnsure 80% of employees are trained in DLP policy compliance by end of quarter
Identify employees needing DLP policy training
Monitor and record employees' training progress
Schedule mandatory DLP compliance training sessions
KRReduce data security incidents by 40% with DLP integration
Implement DLP software across all company systems
Train employees on data loss prevention practices
Continually monitor and update DLP systems as needed
OKRs to establish unparalleled data leak protection solution
ObjectiveEstablish unparalleled data leak protection solution
KRIncrease client satisfaction regarding data security by 25% through feedback surveys
Analyze survey responses for areas of improvement
Develop and execute strategies to address identified issues
Implement consistent client feedback surveys on data security
KRDevelop and implement a cutting-edge encryption system by increasing R&D team by 15%
Execute full implementation of new encryption system
Identify talent to expand R&D team by an additional 15%
Develop advanced encryption system prototype
KRReduce successful cyber attacks on our system by 80%
Implement multi-factor authentication for all system users
Regularly update and patch system software
Conduct frequent cybersecurity training for employees
OKRs to implement cutting-edge bot detection technologies for website data
ObjectiveImplement cutting-edge bot detection technologies for website data
KRAchieve 95% accuracy rate in detecting bots using newly implemented technologies
Continuously refine and update the models deployed
Test algorithms with diverse sets of data
Implement new machine learning algorithms for bot detection
KRIntegrate and test 3 selected bot detection technologies on our website
Choose three suitable bot detection technologies for our website
Conduct thorough testing to ensure effectiveness
Implement these technologies into our site's backend
KRIdentify and study 10 new bot detection methods from industry research
Analyze each method's pros, cons, and applicability
Select 10 recent industry research on bot detection methods
Prepare a report summarizing findings
OKRs to enhance data privacy and cybersecurity measures to safeguard sensitive information
ObjectiveEnhance data privacy and cybersecurity measures to safeguard sensitive information
KRImplement a comprehensive data encryption system across all relevant platforms
Assess current data encryption measures and identify gaps for improvement
Develop and implement a standardized data encryption protocol for all platforms
Conduct regular audits to ensure consistent adherence to the data encryption system
Train employees on proper data encryption practices and its importance in data security
KRConduct regular vulnerability assessments and address identified risks within set timeframes
Quickly prioritize and address identified risks based on severity levels
Schedule regular vulnerability assessments according to established timelines
Establish set timeframes for risk mitigation and ensure timely execution
Develop a clear process for tracking and documenting vulnerability assessment findings
KRIncrease employee awareness and participation in cybersecurity training programs by 25%
Recognize and reward employees who actively participate in cybersecurity training
Create engaging and interactive modules for cybersecurity training programs
Organize lunch and learn sessions to promote employee awareness about cybersecurity threats
Send regular email reminders about upcoming cybersecurity training sessions
KRAchieve a 10% improvement in overall incident response time, ensuring timely mitigation of potential breaches
Streamline incident response processes and eliminate any unnecessary steps for faster response times
Regularly evaluate and improve incident response plans to enhance efficiency and effectiveness
Provide comprehensive training to all personnel involved in incident response procedures
Implement automation tools to expedite the identification and containment of potential breaches
OKRs to implement robust data privacy compliance framework
ObjectiveImplement robust data privacy compliance framework
KRConduct comprehensive audits of 75% of current processes for data privacy compliance
Execute audits on 75% of selected processes for compliance review
Train employees on conducting comprehensive data privacy compliance audits
Identify existing processes and determine which require data privacy audits
KRAchieve 0 data breaches due to non-compliance with privacy regulations
Implement updated privacy regulations organization-wide
Run periodic data protection audits
Conduct regular privacy compliance training
KRTrain 100% of staff on data privacy laws and regulations by quarter end
Develop comprehensive data privacy training program
Schedule mandatory training sessions for all staff
Monitor and confirm staff training completion
Data Security OKR best practices
Generally speaking, your objectives should be ambitious yet achievable, and your key results should be measurable and time-bound (using the SMART framework can be helpful). It is also recommended to list strategic initiatives under your key results, as it'll help you avoid the common mistake of listing projects in your KRs.
Here are a couple of best practices extracted from our OKR implementation guide 👇
Tip #1: Limit the number of key results
Focus can only be achieve by limiting the number of competing priorities. It is crucial that you take the time to identify where you need to move the needle, and avoid adding business-as-usual activities to your OKRs.
We recommend having 3-4 objectives, and 3-4 key results per objective. A platform like Tability can run audits on your data to help you identify the plans that have too many goals.
Tip #2: Commit to weekly OKR check-ins
Having good goals is only half the effort. You'll get significant more value from your OKRs if you commit to a weekly check-in process.
Being able to see trends for your key results will also keep yourself honest.
Tip #3: No more than 2 yellow statuses in a row
Yes, this is another tip for goal-tracking instead of goal-setting (but you'll get plenty of OKR examples above). But, once you have your goals defined, it will be your ability to keep the right sense of urgency that will make the difference.
As a rule of thumb, it's best to avoid having more than 2 yellow/at risk statuses in a row.
Make a call on the 3rd update. You should be either back on track, or off track. This sounds harsh but it's the best way to signal risks early enough to fix things.
Save hours with automated Data Security OKR dashboards
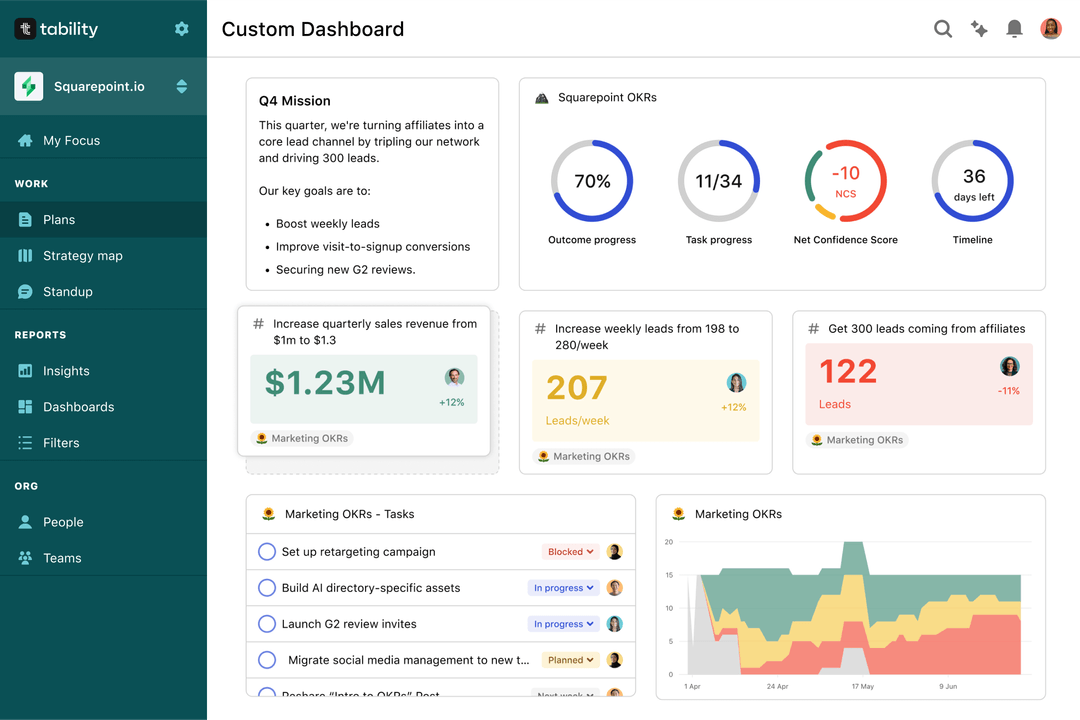
Your quarterly OKRs should be tracked weekly if you want to get all the benefits of the OKRs framework. Reviewing progress periodically has several advantages:
- It brings the goals back to the top of the mind
- It will highlight poorly set OKRs
- It will surface execution risks
- It improves transparency and accountability
Most teams should start with a spreadsheet if they're using OKRs for the first time. Then, you can move to Tability to save time with automated OKR dashboards, data connectors, and actionable insights.
How to get Tability dashboards:
- 1. Create a Tability account
- 2. Use the importers to add your OKRs (works with any spreadsheet or doc)
- 3. Publish your OKR plan
That's it! Tability will instantly get access to 10+ dashboards to monitor progress, visualise trends, and identify risks early.
More Data Security OKR templates
We have more templates to help you draft your team goals and OKRs.
OKRs to enhance leadership effectiveness with my instructors
OKRs to reach $100,000 ARR in app stores without paid marketing
OKRs to validate problem and product hypotheses for MVP
OKRs to enhance profitable performance of the finance team
OKRs to achieve 10% reduction in non-critical inventory stockpile
OKRs to enhance collaboration and stimulate thought leadership